
SUB and CMP are already similar enough in x86, but in Propeller, they are even encoded super similar, to where you can do some stupid assembly syntax to convert one into the other.
This is by far my favorite x86 encoding thing; you can unlock way more functionality with this instruction that requires machine encoding beyond just basic assembly.

Pretty much any insctruction can be a NOP, due to a 'never' condition. ARM is very similar in this way.

Using the FIST instruction as an obfuscation technique, because fisting.
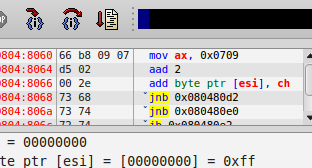
Taking a look at some blank spots in the Intel manuals opcode map.
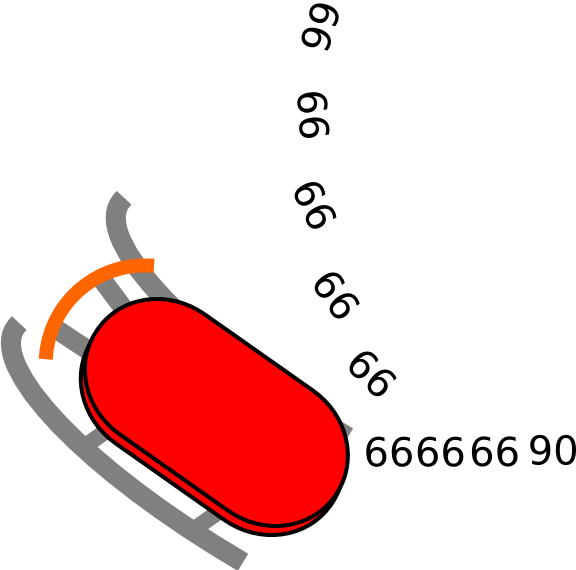
Intel tries to abuse the ModR/M table for variable byte NOPs, read on to see how we can do some better abuse for multibyte NOPs that are also still sledable.
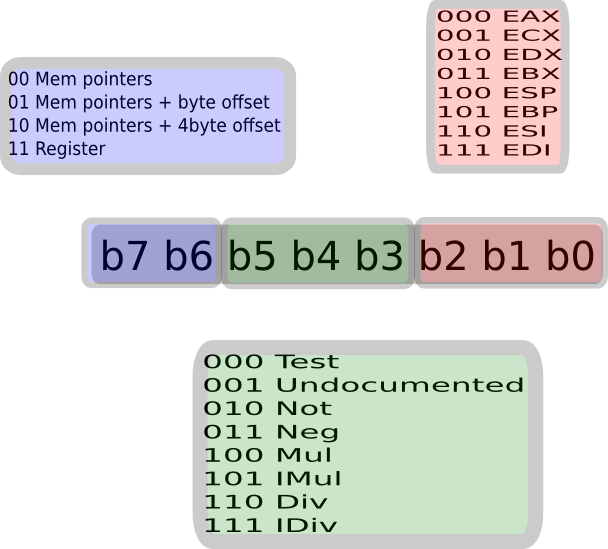
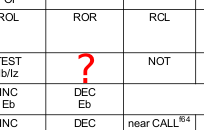
Some instructions have a register (a common one like EAX) hardcoded, but you can still use the non hardcoded encoding and still pick EAX. This offers a redundancy.

SAL is valid assembly, but gets encoded as SHL, yet we can still hardcode the real SAL, and it works as it should!
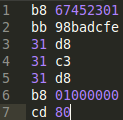
A tutorial/walkthrough on some of my methods of writing code in machine code instead of assembly language.

A breif description of the brain I put into my bass guitar.
XlogicX - Copyright 2022 - Powered by some shitty python scripts









